
5 most common cyber attacks and how to prevent them
Home » Security » 5 most common cyber attacks and how to prevent them
As an organization, small or large, you increasingly find yourself in the sights of a cybercriminal. That’s the harsh reality. They are constantly looking for new ways to steal your sensitive information and compromise your systems. Thankfully, with good cybersecurity, you can get to work protecting your employees and your organization. In this article, we discuss 5 common cyber attacks and give you tips on how to prevent them.
1. Phishing
Phishing is a form of cybercrime in which a malicious user attempts to obtain your personal information. This includes passwords and other sensitive information. They do this by impersonating a trusted source, such as an employee, a supplier or a recognized organization. They can do this through emails, text messages, websites or social media. Their goal is to make money from your data. They may sell it to others or exploit your payment information or passwords.
The numbers don’t lie. Phishing is by far the most common cyber attack because of its high effectiveness and easy configuration for the hacker. They can send a large amount of emails without much effort and hope that someone will fall for it. The number of Phishing emails increased a whopping 569% in 2022.
How does phishing work?
The word Phishing is derived from “fishing” or fishing for information. Unfortunately, they are enormously successful with this simple attack. They do this, for example, by properly drafting the email and in addition, capitalizing on your feelings.
So how do they get your data? They do so by getting you to click on a link. That link redirects you to a malicious website or you download an infected file. If you then leave your data on that website, the loot is in the hands of the attacker. Are you downloading an unknown file? Then malware may be installed unnoticed. We discuss that form of cybercrime further in this blog.
In the example below, you can clearly see that they are capitalizing on the victim’s fears. In addition, they create a sense of urgency by stating that the website will only be available for 72 hours. This may cause you to visit the website out of panic anyway. So the ingredients for a good phishing email are clearly present here:
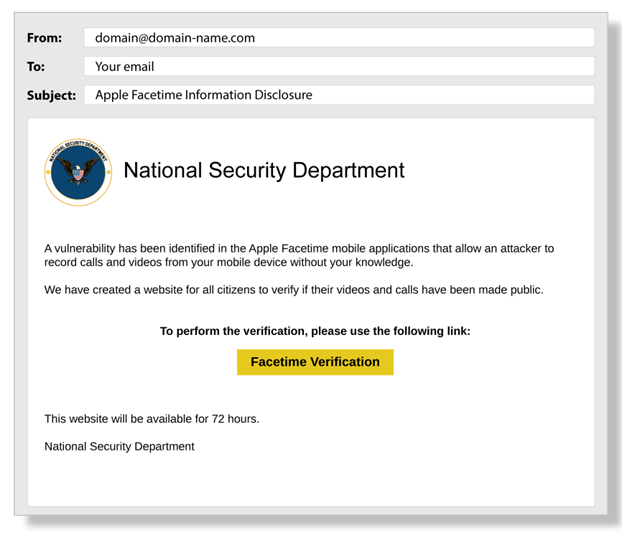
Acknowledged party/reliable source: National Security Department + logo
Capitalizing on your fears: your privacy is compromised and you only have 72 hours to verify.
Malicious link: The big yellow button leads you to a fake website where victims unknowingly leave their data to rogue users
How to avoid phishing
The best way to prevent Phishing is with Cybersecurity Awareness Training. This way, your employees will be able to recognize suspicious emails and take the appropriate action. At Safe-Connect, we provide this solution on a large scale. We can then also put it to the test with a Phishing simulation.
Furthermore, you can use a spam filter and Multifactor Authentication to reduce the risk. By implementing advanced mail protection, you ensure that most phishing emails don’t even reach your mailbox. With Multifactor Authentication, you limit the access in case you do lose your data to hackers. This security measure still requires them to go through another access control such as your authorization via your cell phone or mail.
Ready to secure your organization? With Microsoft, we provide a total solution for your organization and its employees.
Talk to our expertsWhat to do if you are a victim of Phishing?
If you did fall victim to Phishing, it is important to immediately restrict access to affected accounts and change passwords. Make sure your internal communications are on point so you know exactly what went wrong. Next, secure any systems that may have been compromised. This may mean disconnecting them from the network or shutting them down altogether to prevent further damage.
Also, be sure to use a convenient password manager such as Bitwarden. That way you can use a new and strong password for each account. If they then figure out your password, their access to your data is limited to 1 account.
2. Ransomware
Ransomware is a type of malware that prevents you from accessing your files unless you pay a ransom. The cybercriminal accomplishes this with mischievous software that encrypts your files. You may have accidentally downloaded this with a Phishing message. He then informs you that he will lift the encryption as soon as you complete payment. Often he asks for the money in the form of Bitcoin or other cryptocurrency, making it difficult to trace.
Not only has the cybercriminal encrypted your files, he has them completely available for him to read. That can cause a lot of chaos, fortunately there are ways to protect yourself from an attack of this caliber.
How do you prevent ransomware?
The best way to prevent Ransomware is to use multi-layered cybersecurity. At Safe-Connect, we do that by combining Microsoft security with Fortinet’s intelligent firewalls.
With Microsoft’s infrastructure, you enjoy backups in the Cloud which allows you to access your files at any time. That means that in the event of a ransomware attack, you can get back up and running quickly without paying a ransom.
On top of a secure cloud environment, we also choose Intelligent Firewalls by Fortinet. This ensures that your network is also protected against unauthorized users. This way you also limit the access of hackers when they do get in.
A piece of golden advice is to have strong security at all times. That way you are well protected against cybercrime in all areas. By having a cybersecurity plan, you also know what action you can take in the event of an attack.
Curious about how your organization can be secured? Request a free intake interview with one of our experts!
Free call with our specialistsWhat to do if you are a victim of Ransomware?
If you did fall victim to ransomware, it’s recommended you don’t pay. This just encourages cybercriminals to do it more often. Possibly again in your organization. Instead, you can disconnect the affected devices from the network to prevent further spread. In this case, it’s best to reach out to your IT partner to review options together and discuss a solution.
Also, if sensitive data is encrypted such as passwords and bank information, call your bank immediately to tell them the data has been stolen. To minimize the problem of passwords, it is best to reset them and use a reliable password manager such as Bitwarden.
3. Malware
Malware is short for “malicious software,”. It is designed to cause damage to computers, networks and mobile devices. Malware can spread through various channels, including e-mail attachments, fake software updates, pop-up ads and malicious websites.
There are several types of Malware, including:
- Viruses: These are programs that replicate and spread themselves by copying themselves to other files on your computer.
- Trojans: This is Malware that pretends to be legitimate software but actually contains malicious code.
- Worms: These are programs that spread themselves over the network and copy themselves to other computers without user intervention.
- Ransomware: As discussed earlier, this is Malware that encrypts files on a computer. It then demands a ransom to make the files accessible again.
How do you prevent malware?
The most effective way to prevent Malware is to invest in User Awareness Training. This will ensure that your employees become familiar with the possible dangers. As a result, they know what action they can take and how to protect themselves and your organization from digital threats.
In addition, layered security remains crucial to protect your organization at all levels. With our expertise in Microsoft and Fortinet, we provide a total solution here. This ranges from intelligent firewalls to a fully managed work environment. That way, your software is also always up to date.
Find out how we can secure your organization. Schedule a free consultation with one of our security specialists!
Free consultation with our specialistsWhat to do if you are a victim of Malware?
If you did fall victim to malware, it is best to disconnect the affected devices from the network to prevent further spread. Be sure to discuss the situation with your IT partner to find an appropriate solution.
4. DDoS attacks
A Distributed Denial of Service (DDoS) Is a type of cyber attack in which a large volume of requests is sent to a website, server or network, causing it to become overloaded and inaccessible. DDoS attacks can be carried out using a botnet, which is a network of infected computers controlled by a hacker.
How do you prevent a DDoS attack?
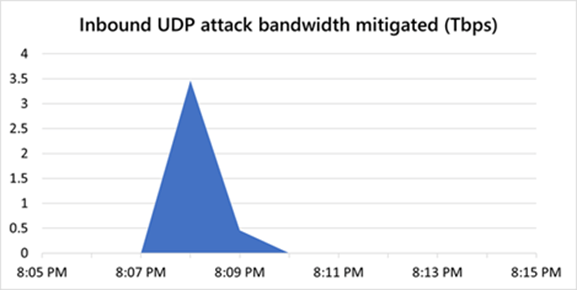
You can’t prevent a DDoS attack. But fortunately, there are many ways to minimize the damage. Microsoft’s Azure platform provides excellent protection against this type of attack. For example, in 2021, they repelled a DDoS attack of 3.47 terabits per second. Because of this protection, the customer was spared financial damage and continuity was guaranteed.
On top of Azure’s advanced security, we also provide your organization with Intelligent Firewalls. These can filter traffic and block unauthorized requests, making it harder to overload your environment.
With smart configurations, we help secure your work environment. Talk to our specialists today!
I want smart cybersecurity!What to do if you are a victim of a DDoS attack?
If you did fall victim to a DDoS attack, you should immediately notify affected parties and Internet service providers to minimize the impact. You can also consider temporarily using another network to maintain the availability of your services.
5. Zero-day attacks
A zero-day attack is an advanced form of cybercrime in which an attacker exploits a vulnerability in software before the developer of the software is aware of the vulnerability. It is “zero-day” because no days (or weeks, or months) have passed since the vulnerability was discovered, and thus there has not yet been time for the developer to release a fix or patch.
This vulnerability can be used by the attacker to gain unauthorized access to a system, steal data or perform other malicious activities. Zero-day vulnerabilities are often sold on the black market or used by sophisticated hackers to launch targeted attacks against specific organizations.
The major problem with a zero-day attack is that the developer is not yet aware of the vulnerability, so there is no solution available to prevent the attack. Once the developer is aware of the vulnerability, they can try to develop a patch to fix it.
How do you prevent a zero-day attack?
Preventing a Zero-day attack requires a lot of expertise. An experienced IT partner such as Safe-Connect is happy to help you meet this challenge.
An important part of protecting your organization from an attack of this caliber is to deploy sandboxing techniques. It works by executing suspicious code or files in an isolated virtual environment. This allows them to be monitored and analyzed without risk to your system. If malicious code or files show up, they are blocked and not allowed in your infrastructure. The sandbox technique is an effective way to detect and prevent zero-day attacks.
It is also important to perform constant updates. That’s because these vulnerabilities are often found in outdated versions. With Microsoft and Scappman, we have the tools and expertise to make sure all your software stays up-to-date.
To further protect against a Zero-day attack, you need a solid cybersecurity strategy. That way, your organization is still well prepared with a solid infrastructure. This is equipped with smart security solutions that keep you well protected. By deploying Artificial Intelligence, we also quickly detect where the vulnerability occurred. With those insights, we go to work to solve the problem.
What to do when you are a victim of a Zero-day attack?
If your organization has been caught by a zero-day attack, the first thing to do is to find out where the vulnerability occurred. Then you can communicate with your IT partner and the vendor of the vulnerable software. They will then review further options and work on a patch to fix the flaw.
Multi-layered cybersecurity remains critical
Preventing cyber attacks is critical for businesses of all sizes. By regularly implementing security procedures and training, companies can reduce their risk of cyber attacks and ensure the security of their data and systems. In the event that an attack does occur, it is important to respond quickly and take appropriate steps to minimize the impact and prevent the attacker from being able to strike again. Remember, cyber security is an ongoing effort and it is important to always stay abreast of the latest threats and solutions.
Ready for an advanced cybersecurity strategy? We'd love to help you move forward with this challenge. Schedule a free consultation with one of our specialists today!
I opt for advanced cybersecurity