An overview of different types of Phishing
Home » Security » An overview of different types of Phishing
Phishing remains one of the most dangerous forms of cyber attacks for your organization. This devious practice uses deceptive communications to extract your sensitive information. In this blog, we will guide you through the different forms of Phishing, explain how you can protect yourself, and show some case studies where companies and individuals fell prey to these cunning tactics.
The best way to protect your organization is with Cybersecurity Awareness Training. That’s because Phishing attacks capitalize on human error.
Email Phishing
E-mail Phishing is an attack technique in which attackers send fake e-mails that look like messages from legitimate organizations. The goal is to trick victims into sharing personal information.
Protection
- Verify the sender of the e-mail.
- Check the URLs in the e-mail.
- Do not click on suspicious links.
- Use a reliable antivirus and antiphishing software.
Example of Email Phishing:
In 2014, Sony Pictures Entertainment was hit by a large-scale email phishing attack. Employees received fake emails that appeared to come from known contacts. As a result, sensitive company data was stolen, including confidential emails, financial data and employees’ personal information.
Spear phishing
Spear Phishing specifically targets individuals and uses personal information to make the attack more credible. This may include, for example, information about the victim’s job title.
Protection
- Be careful when sharing personal information online.
- Verify the identity of the sender before sharing sensitive information.
- Use security software to filter suspicious messages.
Example of Spear Phishing:
In 2016, John Podesta, Hillary Clinton’s campaign manager, became a victim of Spear Phishing. He received a fake email that appeared to come from Google and was tricked into sharing his login credentials. This gave the attackers access to thousands of emails, leading to large-scale data breaches during the U.S. presidential election.
Clone phishing
Clone Phishing involves duplicating a legitimate email with a malicious attachment or link. The forged e-mail resembles a previously received message to gain the victim’s trust.
Protection
- Be diligent when opening messages you have received before.
- Check the sender and URLs in the e-mail carefully.
Example of Clone Phishing
In 2017, Netflix employees were targeted by Clone Phishing. They received forged emails that appeared identical to previous communications from their HR department. The attacker sent altered versions of previous messages and managed to obtain employee login credentials.
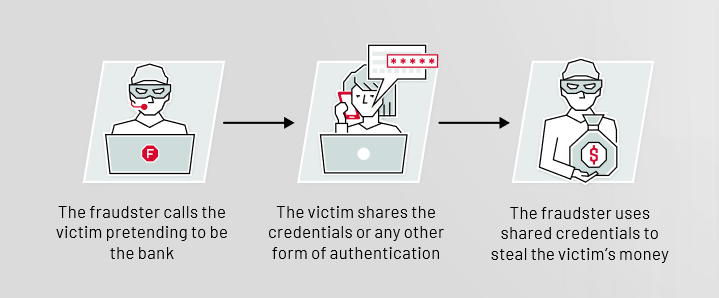
Vishing (voice phishing)
Vishing uses phone calls to trick victims into obtaining personal information. Attackers may pose as official agencies or companies.
Protection
- Be cautious about sharing personal information over the phone.
- Verify the identity of the caller.
Example Vishing:
A major international company, Bank of America, was hit by a Vishing attack in 2020. Customers received phone calls asking them to share their login information because of alleged security problems. This gave the attackers access to bank accounts and personal information. Just recently, casino giant MGM was also completely taken down by a Vishing attack
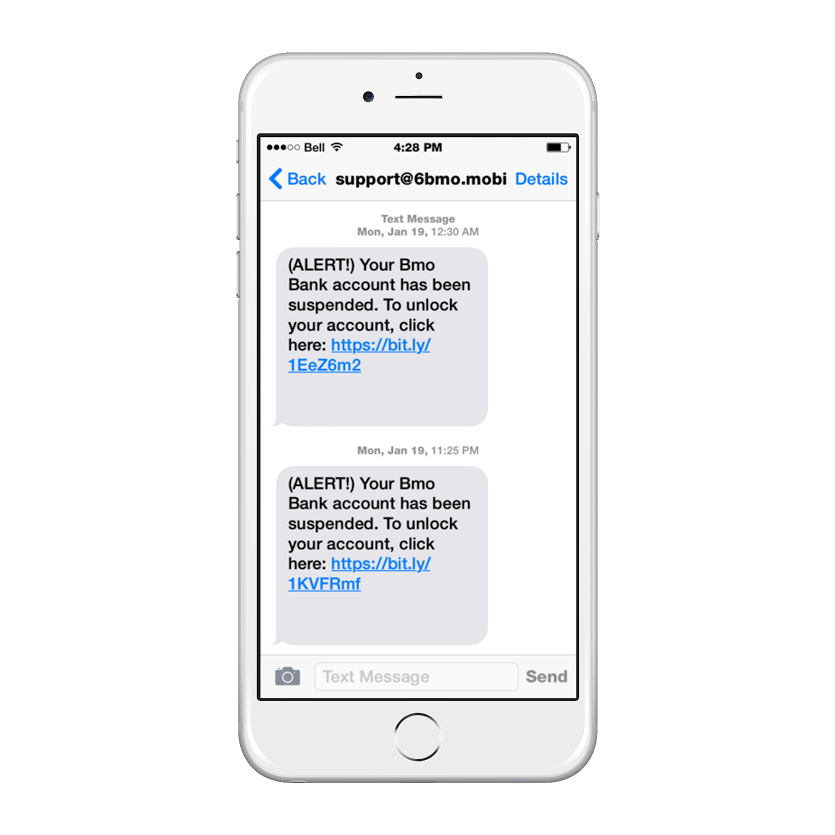
Smishing (SMS phishing)
Smishing is similar to email phishing, but uses text messages to lure victims to counterfeit websites.
Protection
- Do not click on links in suspicious SMS messages.
- Be careful when sharing personal information via SMS.
Example of Smishing
In 2018, Rabobank customers faced smishing. They received fake text messages claiming to be from the bank and asking to confirm login credentials. Customers who clicked on the link gave their details to the attackers.
Whaling
Whaling is an advanced form of phishing targeting high-level positions within an organization, such as CEOs or CFOs. The attackers try to obtain sensitive business information or financial data.
Protection
- Awareness and training of senior officials on phishing risks.
- Implement strict authentication and authorization measures for sensitive information.
- Use encrypted communication channels for sensitive information.
Example of Whaling:
In 2016, Ubiquiti Networks CEO Robert Pera was the victim of a whaling attack. The attackers posed as suppliers and requested payments for nonexistent invoices. As a result, the company lost millions of dollars.
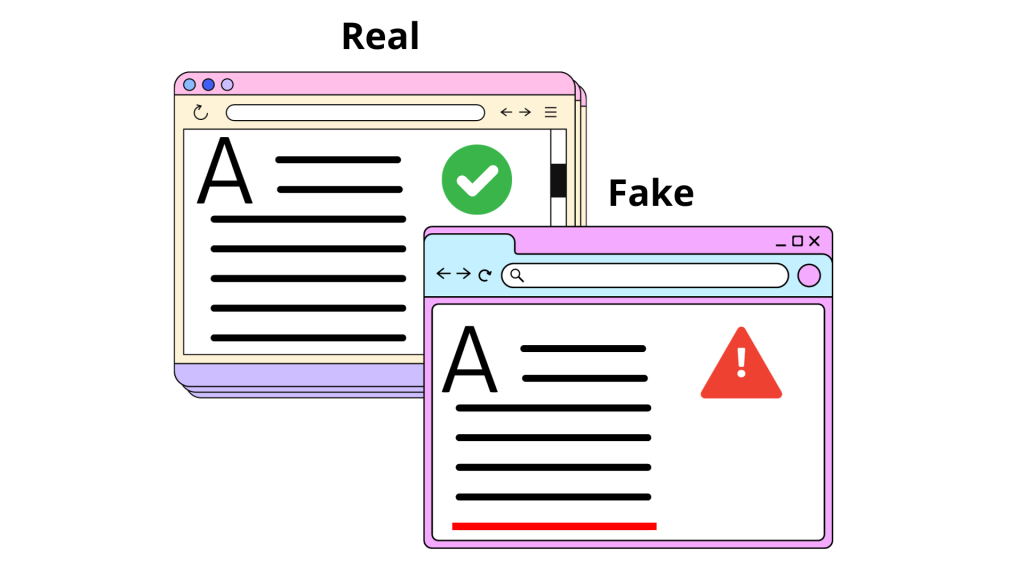
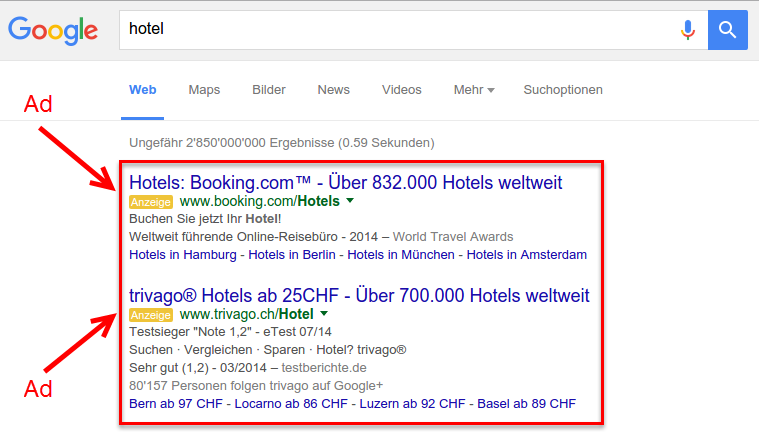
Search Engine Phishing
In search engine phishing, attackers create fake websites that rank high in search results, allowing victims to accidentally visit them instead of the real website.
Protection
- Be careful when clicking on search results, especially if the URL looks suspicious.
- Always enter important websites manually in the address bar rather than through search engines.
Example of Search Engine Phishing:
In 2019, Amazon Marketplace users faced search engine phishing. Fake sellers created websites that ranked high in search results and lured customers to counterfeit product pages. Customers who bought here lost their money without actually receiving a product.
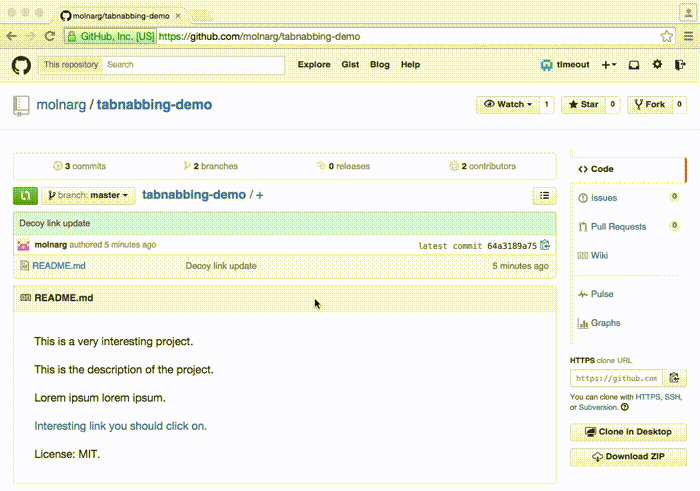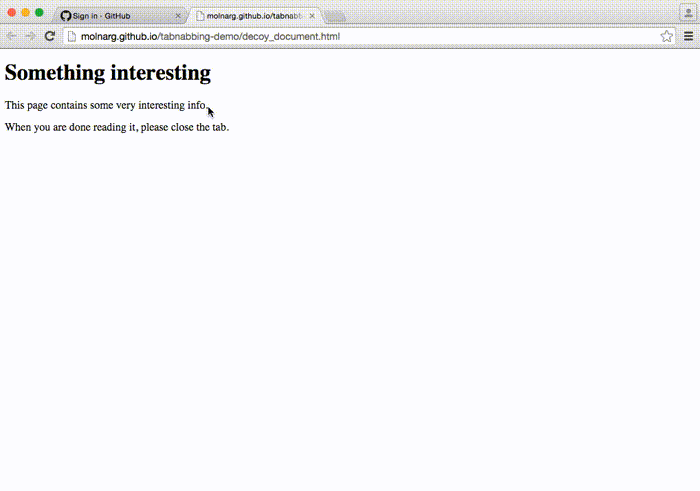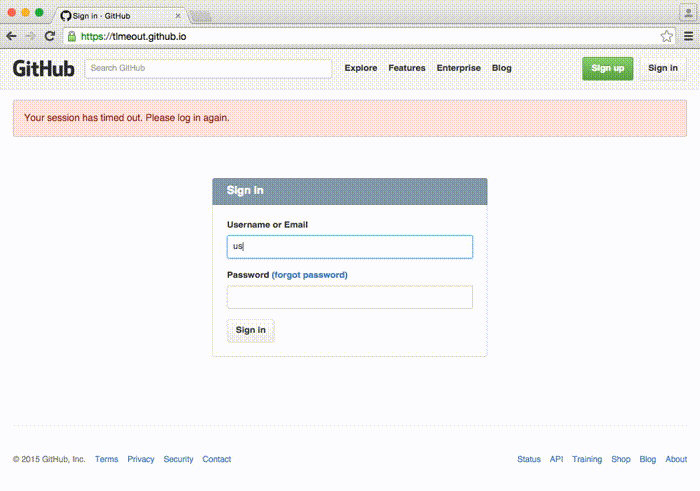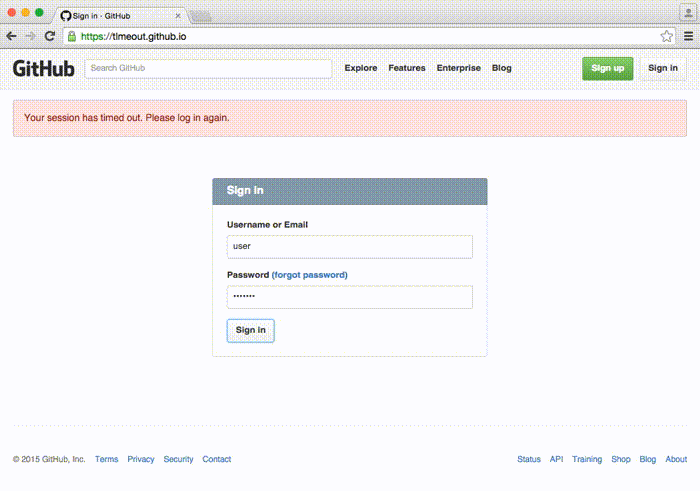
Tabnabbing
Tabnabbing is an advanced form of phishing in which the attacker manipulates an opened browser page to look like a legitimate website after the user has opened another tab.
Protection
- Watch for unexpected changes to open tabs.
- Always check the URL of a page, even if you think you are already on a trusted Web site.
Example of Tabnabbing:
In 2015, Facebook users faced a tabnabbing attack. The attacker manipulated opened tabs to look like Facebook’s login page. Users who logged in again gave their login credentials to the attacker.
Malware-based Phishing
Malware-based phishing uses malicious software (malware) to steal sensitive information from the victim.
Protection
- Keep your operating system, antivirus and anti-malware software up-to-date.
- Avoid downloading suspicious attachments or software from unknown sources.
Example of Malware-based Phishing:
In 2017, the U.S. healthcare company Anthem was hit by malware-based phishing. Employees received emails with infected attachments that distributed malicious software. This allowed the attackers to access personal health data of millions of customers.
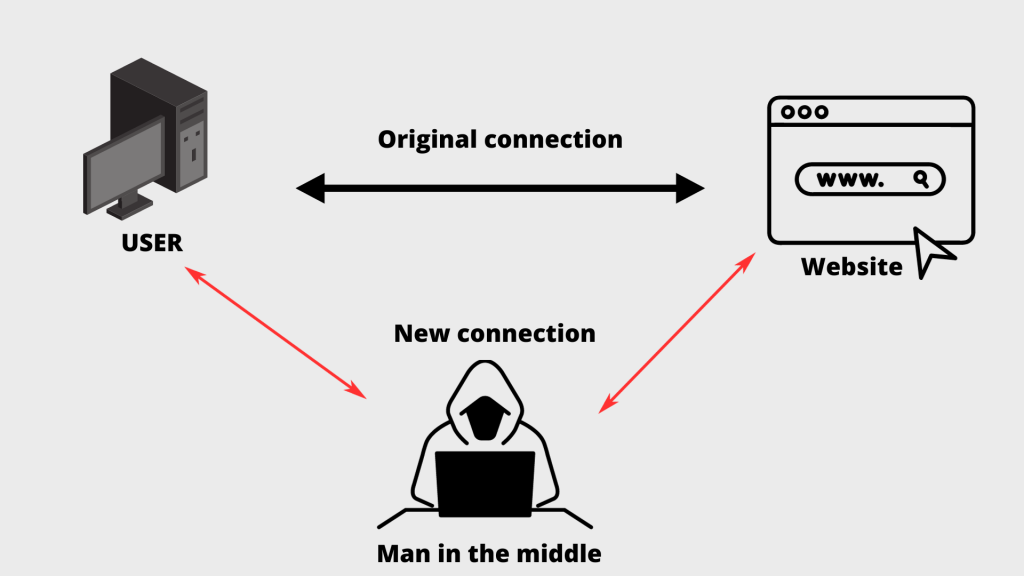
Man-in-the-Middle (MitM) phishing
In MitM phishing, an attacker places himself between the user’s communication and the legitimate website, allowing the attacker to intercept the information.
Protection
- Always use a secure (HTTPS) connection when entering sensitive information.
- Use a VPN (Virtual Private Network) for added security when using public networks.
Example of Man-in-the-Middle (MitM) phishing:
In 2018, a public Wi-Fi network in Times Square, New York, was compromised. Travelers who connected were redirected to forged login pages of well-known social media sites. As a result, login credentials were intercepted and misused by the attacker.