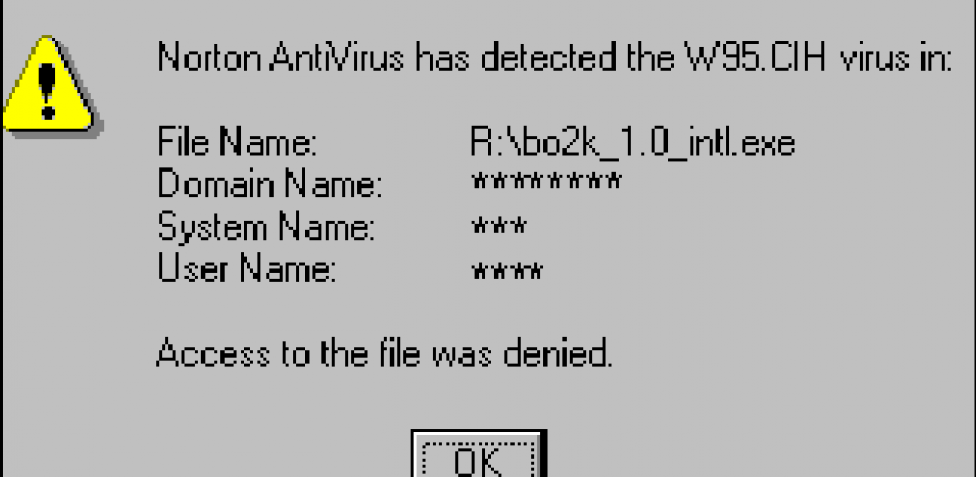
Last Updated on July 18, 2024 The first concepts of self-replicating software In 1949, Hungarian scientist and mathematician John von Neumann laid the theoretical foundation for what we now know as computer viruses. In his lectures at the University of Illinois, published in 1966 under the title “The Theory of Self-Reproducing Automata,” he described how…