Home » Blog overviewLast Updated on January 12, 2026 AI-driven attacks: faster, smarter and more scalable AI didn’t just help defenders move …
Explore the world of IT with Safe-Connect's blog overview!
Home » Blog overviewLast Updated on December 30, 2025 Sometimes the biggest threat is already on your network without you even realizing …
Home » Blog overviewLast Updated on December 17, 2025 What is life like as an Azure Support Engineer? My name is Yunus, …
Home » Blog overviewLast Updated on November 26, 2025 New threats are emerging at a rapid pace. The reflex response is often …
Home » Blog overviewLast Updated on November 14, 2025 Some stories are so absurd that they seem almost funny. Until you realize …
Home » Blog overviewLast Updated on October 29, 2025 It can happen to anyone. An email that looks trustworthy, a link that …
Home » Blog overviewLast Updated on October 1, 2025 Not every employee needs to be able to do everything. Yet in many …
Home » Blog overviewLast Updated on September 26, 2025 Cybercriminals are becoming smarter, faster, and more creative. However, you don’t need complicated …
Home » Blog overviewLast Updated on September 3, 2025 A good password policy is essential for every organization. However, it often remains …
Home » Blog overviewLast Updated on August 21, 2025 Series: From baseline measurement to strong cybersecurity – Part 3 In Blog 2, …
Home » Blog overviewLast Updated on September 15, 2025 Series: From baseline measurement to strong cybersecurity – Part 2 In Blog 1 …
Home » Blog overviewLast Updated on August 20, 2025 Series: From baseline measurement to strong cybersecurity – Part 1 Want to improve …
Home » Blog overviewLast Updated on August 1, 2025 How harmony in chaos ensures safety and ease of use It started innocently …
Home » Blog overviewLast Updated on July 16, 2025 Phishing simulations have a bad reputation among some organisations. Not because they aren’t …
Home » Blog overviewLast Updated on April 2, 2025 Cybersecurity and GDPR are often seen as two separate worlds. On one side: …
Home » Blog overviewLast Updated on February 13, 2025 Shady characters online pull off countless tricks to trap unsuspecting victims. One of …
Home » Blog overviewLast Updated on February 13, 2025 Time for a new chapter in AI regulation. After GDPR, the DMA and …
Home » Blog overviewLast Updated on February 17, 2025 Cybercriminals are constantly searching for new ways to target their victims. A recent …
Home » Blog overviewLast Updated on January 17, 2025 Phishing is a term that unfortunately needs little introduction these days. Yet cybercriminals …
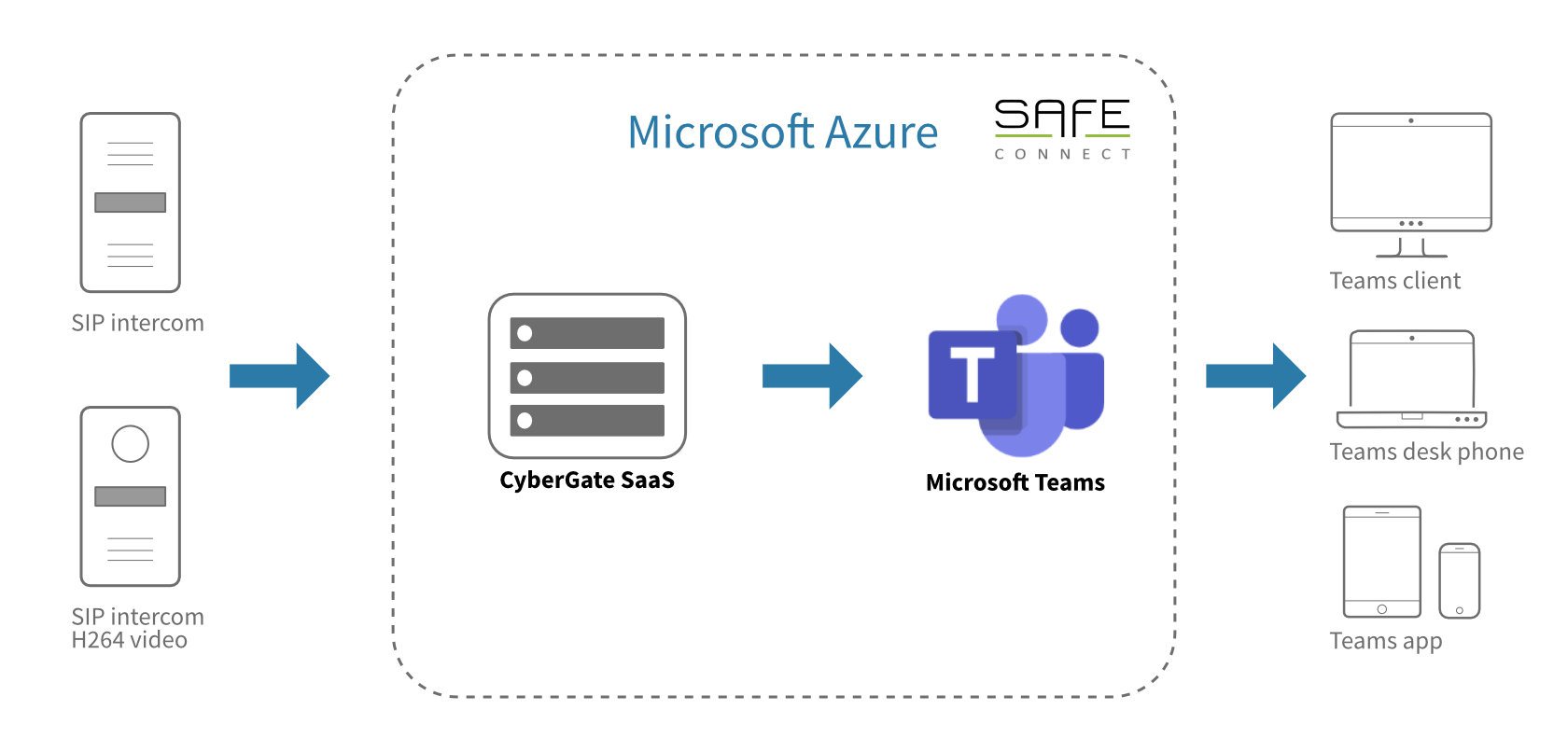
Home » Blog overviewLast Updated on March 18, 2025 Find out how we did it Connecting a smart door intercom to Microsoft …
Home » Blog overviewLast Updated on September 3, 2025 Cyber threats are a reality that every organization faces today. With the introduction …
Home » Blog overviewLast Updated on February 17, 2025 Do you think your organisation is exempt from the NIS2 directive? You may …
Home » Blog overviewLast Updated on December 3, 2024 Smart devices, software, robot vacuums. These technologies make life easier, perhaps too easy. …
Home » Blog overviewLast Updated on October 4, 2024 Artificial intelligence (AI) is no longer just a thing of the future. It …
Home » Blog overviewLast Updated on September 19, 2024 We all make mistakes from time to time. Maybe you accidentally click on …
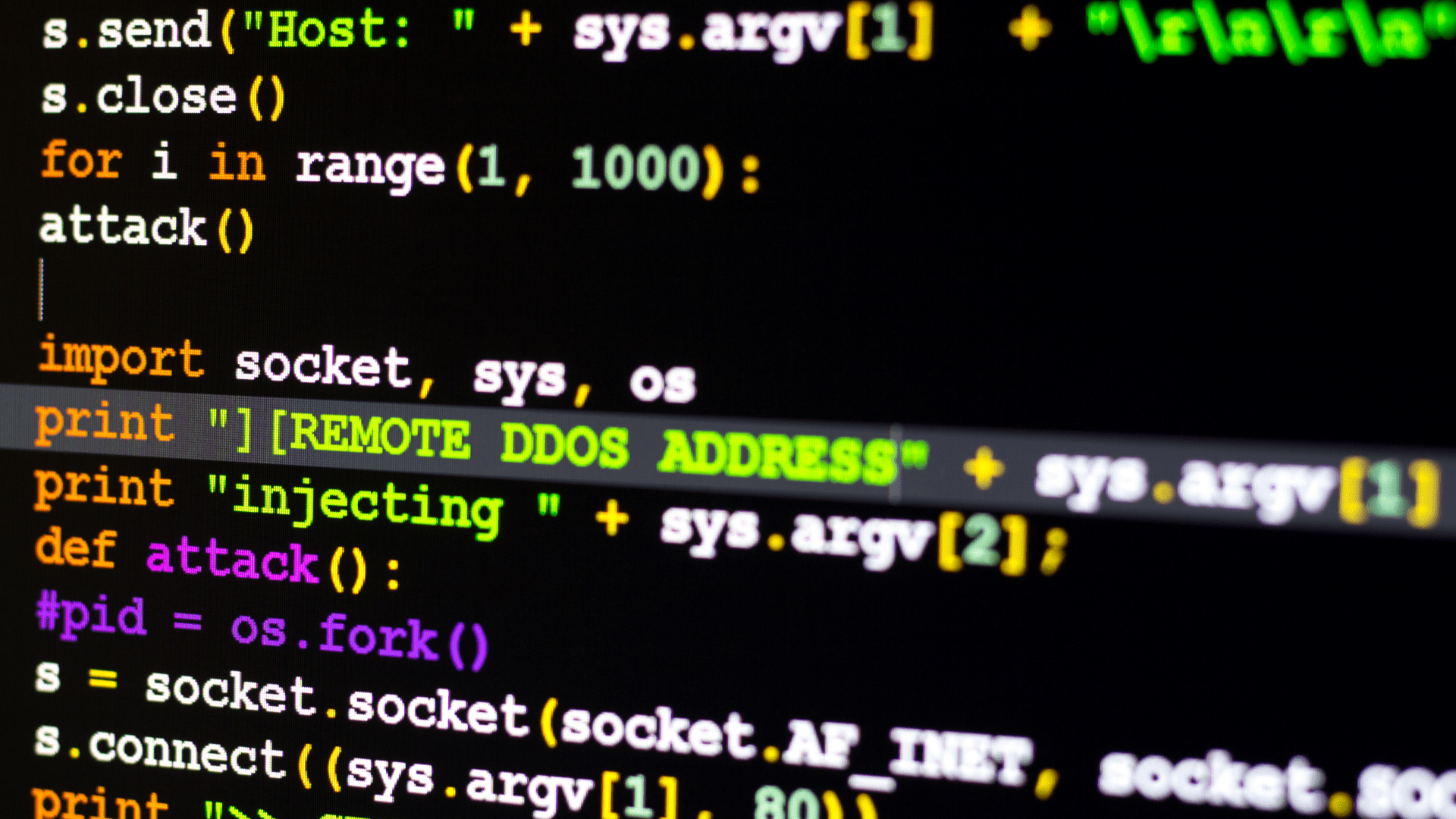
Home » Blog overviewLast Updated on July 18, 2024 The first concepts of self-replicating software In 1949, Hungarian scientist and mathematician John …
Home » Blog overviewLast Updated on July 3, 2024 Ready to make your working day easier and more enjoyable with Microsoft 365 …
Home » Blog overviewLast Updated on April 18, 2024 ChatGPT and other generative ai tools are capable of quickly generating texts and …
Home » Blog overviewLast Updated on March 27, 2024 Useful Ai tools have become a part of our lives. They help us …
Home » Blog overviewLast Updated on March 21, 2024 Cyber threats are constantly evolving. Incident reporting is an essential part of an …
Home » Blog overviewLast Updated on March 20, 2024 In the ongoing evolution of technology, AI models such as ChatGPT are a …
Home » Blog overviewLast Updated on March 18, 2024 Nowadays, online security is really a thing. You often hear about hacks, data …
Home » Blog overviewLast Updated on March 4, 2024 Cybersecurity is one of the biggest challenges for organisations in the 21st century. …
Home » Blog overviewLast Updated on April 25, 2024 The NIS2 Guideline is a new European legislation that aims to improve cybersecurity …
Home » Blog overviewLast Updated on February 8, 2024 In the age of digitalisation and technological advancement, the fight against cybercrime has …
Home » Blog overviewLast Updated on February 2, 2024 Businesses and users log in daily to access information and programs. We constantly …
Home » Blog overviewLast Updated on December 19, 2023 The end of 2023 is in sight. In recent months, we saw a …
Home » Blog overviewLast Updated on December 14, 2023 Writing effective prompts for AI tools such as Bing Chat and ChatGPT is …
Home » Blog overviewLast Updated on December 11, 2023 Microsoft is taking the lead in making Artificial Intelligence (AI) accessible to a …
Home » Blog overviewLast Updated on March 14, 2024 Microsoft’s AI train is gaining momentum. And to top it off, Microsoft Ignite …
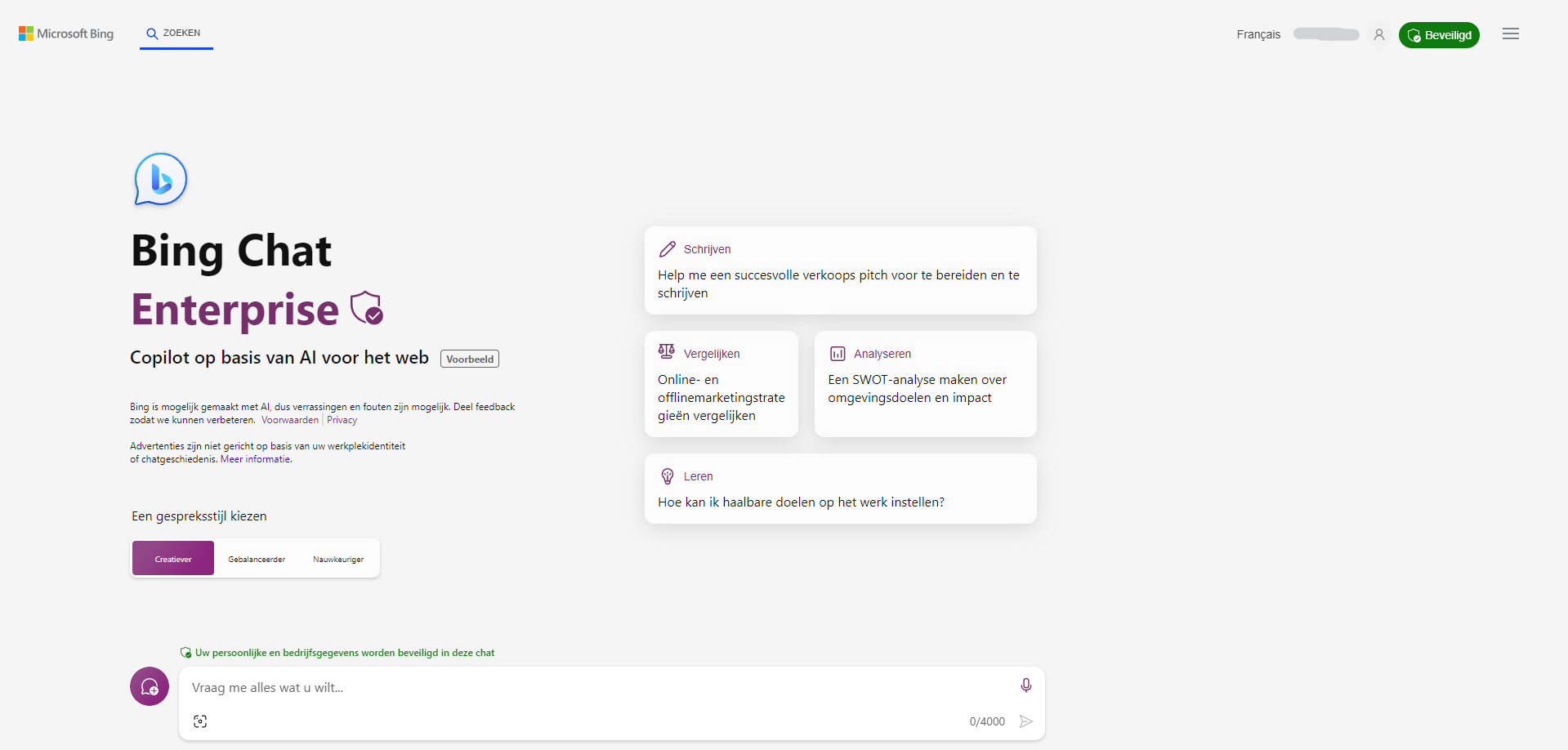
Home » Blog overviewLast Updated on November 30, 2023 Bing Chat was born in Microsoft Edge in February 2023, and its birth …
Home » Blog overviewLast Updated on September 27, 2023 Phishing remains one of the most dangerous forms of cyber attacks for your …
Home » Blog overviewLast Updated on September 22, 2023 Phishing remains popular and comes in all shapes and sizes. Vishing, or Voice …
Home » Blog overviewLast Updated on September 18, 2023 In the world of cyber threats, it is important to be well-informed about …
Home » Blog overviewLast Updated on September 14, 2023 In an era where cyber threats are constantly evolving, it is essential to …
Home » Blog overviewLast Updated on September 27, 2023 Phishing continues to be a prominent cyber attack. More and more people are …
Home » Blog overviewLast Updated on January 24, 2024 Are you familiar with the new NIS2 yet? It is the successor to …
Home » Blog overviewLast Updated on February 13, 2024 As an organization, small or large, you increasingly find yourself in the sights …
Home » Blog overviewLast Updated on August 4, 2023 Public Cloud, a term that has been gaining traction in recent years. That’s …
Home » Blog overviewLast Updated on August 4, 2023 Collaborate securely across devices in multiple locations. Is your way of working digitally …
Home » Blog overviewLast Updated on August 4, 2023 Working safely and productively both in the office and remotely? You can! In …
Home » Blog overviewLast Updated on March 31, 2023 Are you looking for a virtual workplace solution for your employees? Virtual Desktops …
Home » Blog overviewLast Updated on August 4, 2023 The rollout of 5G networks is driving significant changes in the way we …
Home » Blog overviewLast Updated on March 15, 2023 A cybersecurity assessment is an important tool for identifying vulnerabilities and improving the …
Home » Blog overviewLast Updated on August 4, 2023 Is your organisation ready for digital danger? A zero-day attack or zero-hour threat …
Home » Blog overviewLast Updated on August 4, 2023 In the event of a cyberattack, are you sure you can recover your …
Home » Blog overviewLast Updated on March 15, 2023 Are you ready for your Cybersecurity Assessment? In this blog, you’ll discover 5 …
Home » Blog overviewLast Updated on November 5, 2024 In the digital age, cybersecurity is a critical concern for individuals, businesses and …
Home » Blog overviewLast Updated on August 4, 2023 A cybersecurity audit and a cybersecurity assessment are two tools used to evaluate …
Home » Blog overviewLast Updated on August 4, 2023 Outsourcing cybersecurity can bring many benefits to your business. In this blog, you’ll …
Home » Blog overviewLast Updated on March 15, 2023 Programmable Logic Controllers (PLCs) are computer-based systems that are used to control industrial …
Home » Blog overviewLast Updated on March 15, 2023 Talk about a hot topic! With energy prices increasingly in the spotlight, organizations …
Home » Blog overviewLast Updated on August 9, 2023 Cybercrime is now also causing a stir in cities and municipalities. Antwerp and …
Home » Blog overviewLast Updated on August 4, 2023 Cybersecurity is indispensable for businesses. Attack strategies are constantly evolving so being up-to-date …
Home » Blog overviewLast Updated on March 15, 2023 Strong basic security is a regulatory requirement. That starts with digital hygiene training …
Home » Blog overviewLast Updated on August 4, 2023 Say goodbye to a plethora of cables USB C will become the standard …
Home » Blog overviewLast Updated on August 4, 2023 With Microsoft Azure, we monitor part of your IT infrastructure. This results in …
Home » Blog overviewLast Updated on August 4, 2023 The security software that turned out to be unsecure for 10 years. Avast …
Home » Blog overviewLast Updated on August 4, 2023 Are you enjoying strong passwords with Bitwarden yet? The trusted password manager has …
Home » Blog overviewLast Updated on August 4, 2023 Tech companies and Open Source projects aim for the highest level of security. …
Home » Blog overviewLast Updated on August 4, 2023 We are working more and more in a digital environment. This is accompanied …
Home » Blog overviewLast Updated on May 30, 2024 The 5 biggest advantages of connecting a legacy system like AS400 to Azure …
Home » Blog overviewLast Updated on May 30, 2024 As a company, it is important to set up proper security in Microsoft …
Home » Blog overviewLast Updated on August 4, 2023 In November 2021, the Azure DDoS protection platform managed to deflect an attack …
Home » Blog overviewLast Updated on August 4, 2023 A disturbing trend in recent years has been the increase in cybercrime. Previously, …
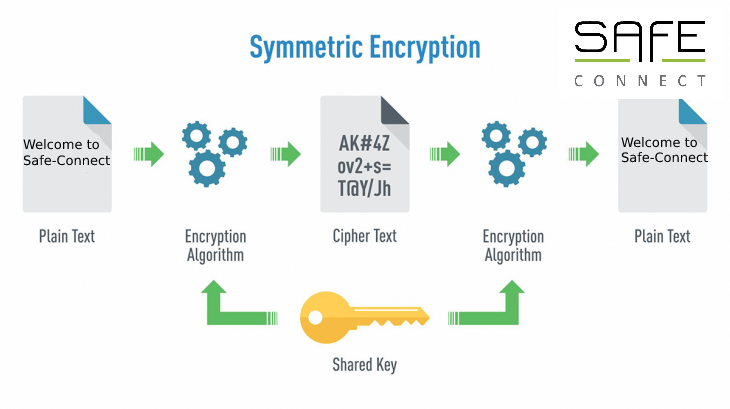
Home » Blog overviewLast Updated on May 30, 2024 You’ve probably heard of End-to-end Encryption before. Especially if you use Whatsapp regularly. …
Home » Blog overviewLast Updated on August 4, 2023 The black and white code that experienced its growth during the pandemic; is …
Home » Blog overviewLast Updated on May 16, 2024 Microsoft offers several licenses aimed at businesses and organizations. Plenty of choice! But …
Home » Blog overviewLast Updated on September 27, 2023 Users are increasingly exposed to cybercrime. Phishing is the most popular method of …
Home » Blog overviewLast Updated on March 15, 2023 Do you also get flooded with emails in the Outlook Web App every …
Home » Blog overviewLast Updated on August 4, 2023 At Safe-Connect, we recognized the importance of good air quality in office spaces. …
Home » Blog overviewLast Updated on August 4, 2023 What is Log4j and are you affected? There is a major security risk …
Home » Blog overviewLast Updated on August 4, 2023 The digitization created new ways of working. Although it offers many advantages, there …
Home » Blog overviewLast Updated on May 30, 2024 Combining cybersecurity and productivity doesn’t have to be a barrier for your organization. …
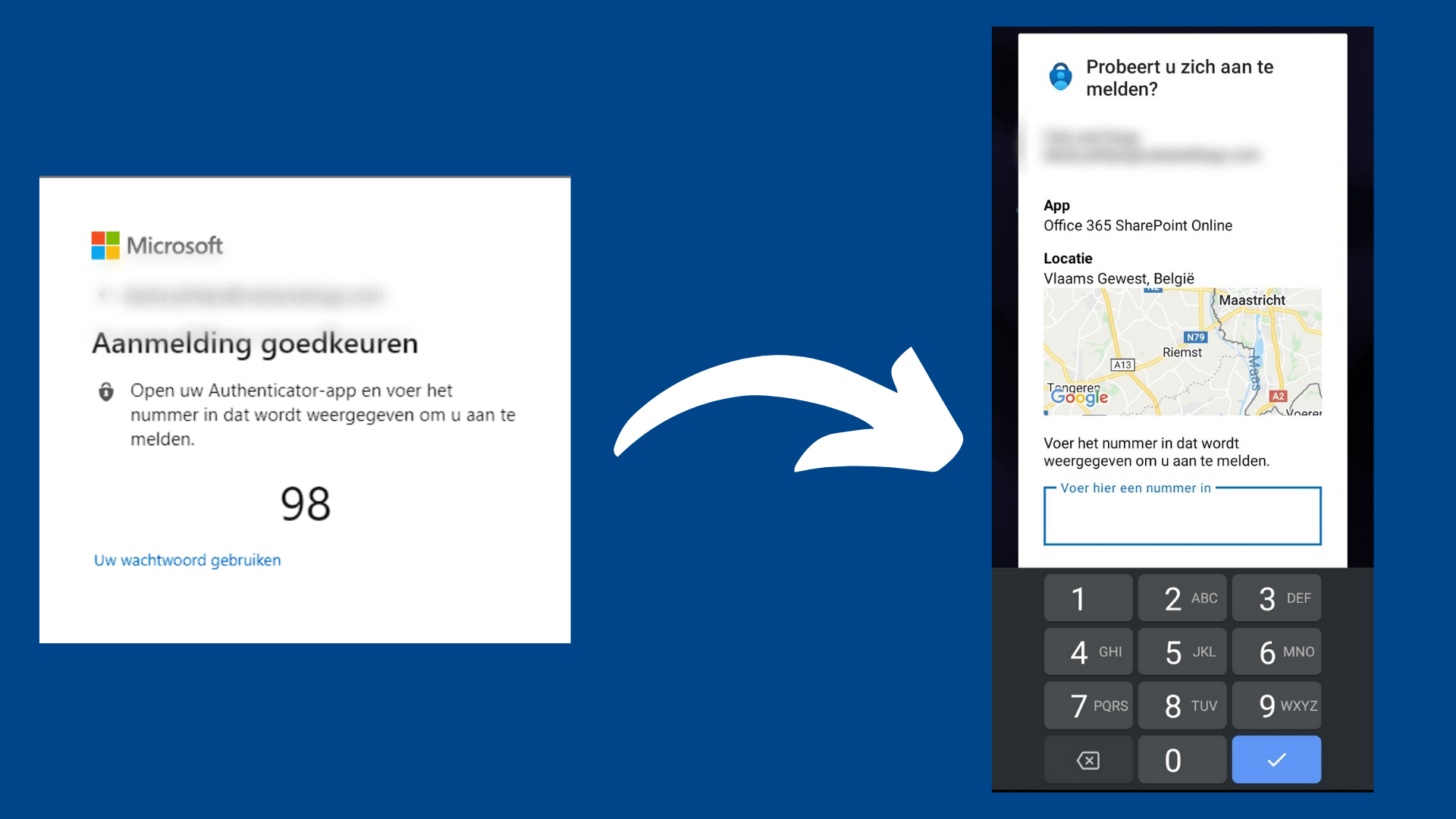
Home » Blog overviewLast Updated on May 30, 2024 Multifactor authentication is necessary to protect us in a digital environment. You can …
Home » Blog overviewLast Updated on May 30, 2024 Our platforms or devices that we use on a daily basis, have many …
Home » Blog overviewLast Updated on May 29, 2024 In order to work with different programs or websites, we first need to …
Home » Blog overviewLast Updated on March 15, 2023 It’s time for Windows 11! Without a doubt, you’ve heard about it. The …
Home » Blog overviewLast Updated on September 24, 2025 Alarming news in the world of cybersecurity. Vulnerabilities in Microsoft Exchange servers allowed …
Home » Blog overviewLast Updated on September 24, 2025 It’s becoming increasingly more common. Data breaches, companies being hacked and important information …
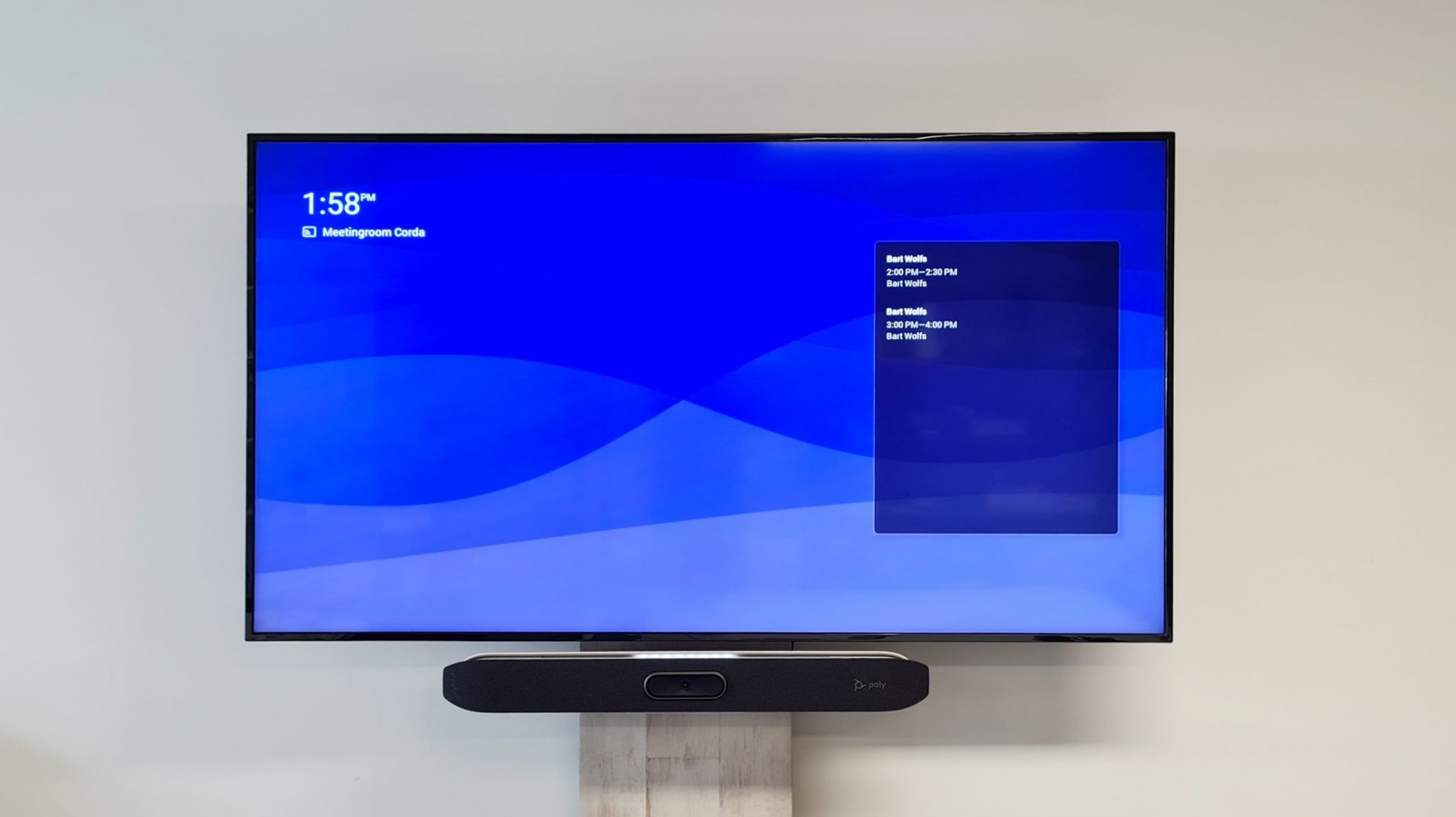
We are increasingly using software such as Teams or Zoom to organise meetings. This is certainly no surprise in a digital Covid era. Video conferencing is becoming increasingly more common. Unfortunately, it can sometimes be difficult to appear professional when the audio and video quality is not optimal. Does this sometimes bother you during important meetings? Fortunately, there is a solution that offers very good video and audio performance and also eliminates cable clutter. At Cats & Dogs, we put it to the test and tested the PolyX50.
Home » Blog overviewLast Updated on May 30, 2024 Telephony in Teams, is it possible? Microsoft Teams offers usability and many features …
Home » Blog overviewLast Updated on August 4, 2023 On the 25th of May 2018, GDPR became law. Yes, that’s almost 2 …
Home » Blog overviewLast Updated on March 15, 2023 The FIRST® LEGO® League is a robot competition for youths aged 11 to 14. The competition …