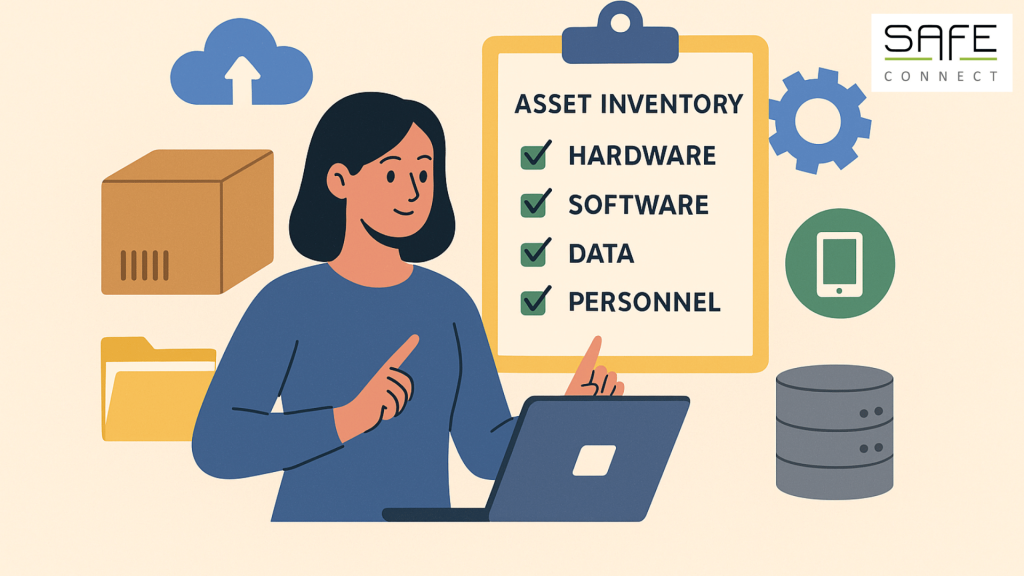
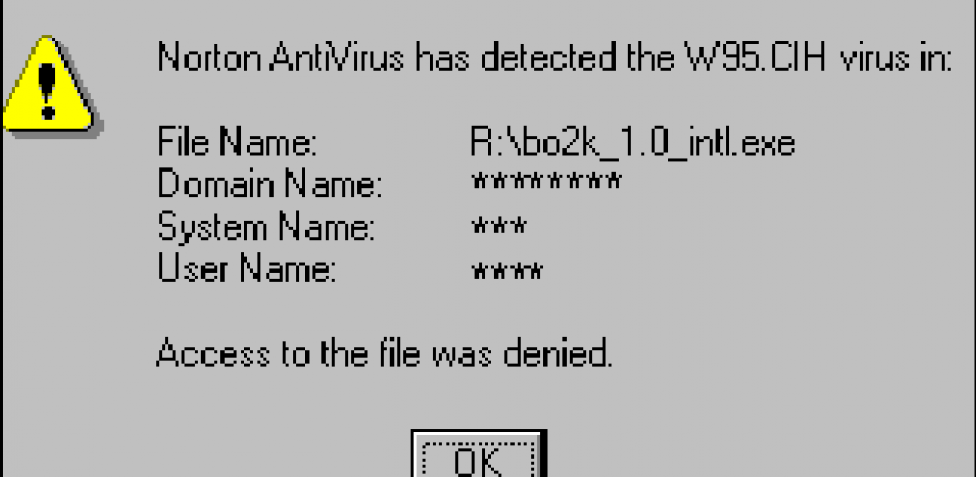
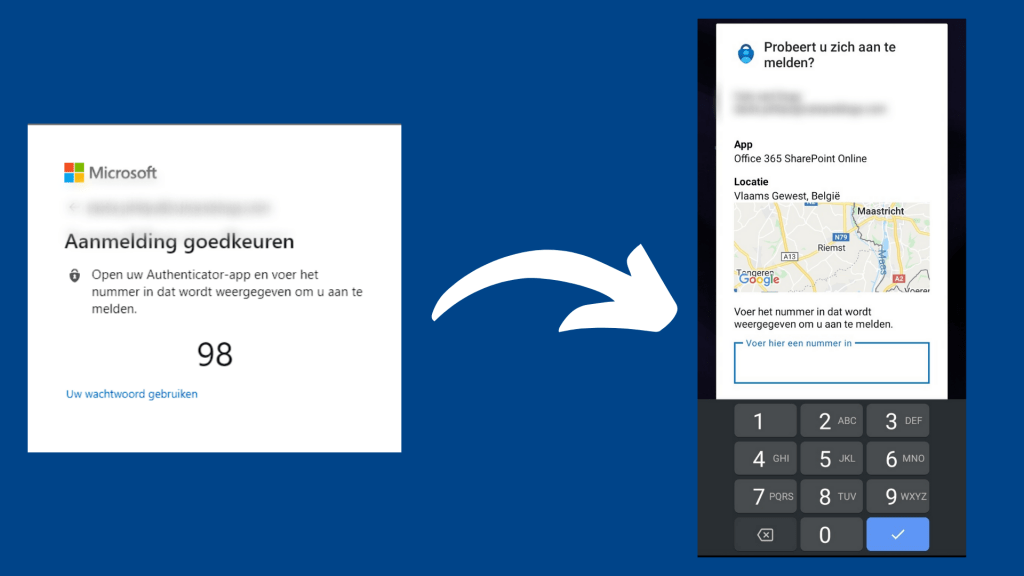
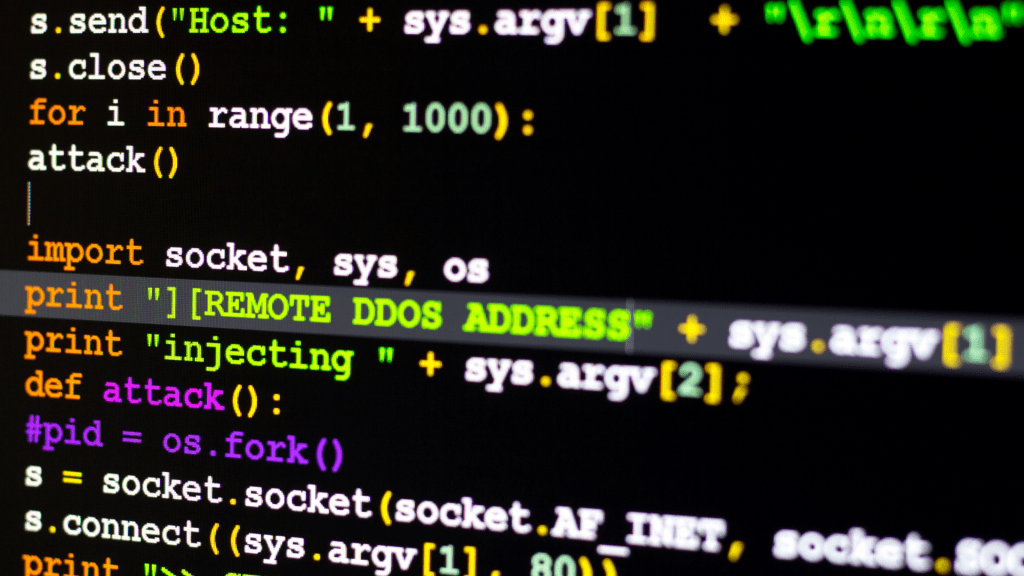
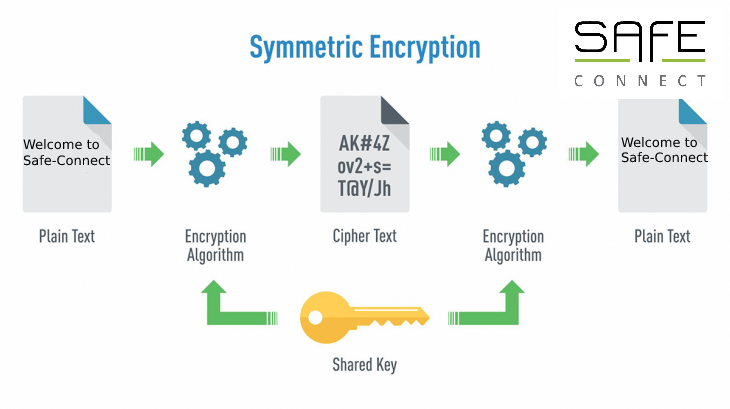
Last Updated on January 12, 2026 AI-driven attacks: faster, smarter and more scalable AI didn’t just help defenders move forward this year. Attackers embraced it just as eagerly. Large language models were used to write malware, personalize phishing campaigns and exploit vulnerabilities at greater speed. Some malware even adapted automatically to the victim’s environment. Predictable…