How to create a complete asset inventory
Home » Security » How to create a complete asset inventory
In Blog 1 of this series, you discovered why an asset inventory combined with a risk assessment is the best first step toward strong cybersecurity.
Today, we will focus on steps one and two: creating your asset inventory and classifying your assets.
What is an asset inventory?
An asset inventory is an overview of everything that is important to your organization. That means more than just laptops and servers.
Consider:
- Hardware: laptops, servers, network equipment, mobile devices
- Software: applications, cloud solutions, licenses
- Data: customer data, internal documents, intellectual property, resumes
- People: employees, partners, suppliers
Tip: don’t forget your invisible assets. Think of API connections, SaaS subscriptions, and external data centers. These are often just as crucial, and sometimes even more vulnerable, than the hardware on your desk.
How do you approach it?
- Collect information automatically wherever possible
Use your IT management tools to map hardware and software. - Supplement with interviews and checklists
Not everything is detected automatically. Talk to IT, departments, and suppliers to fill in any missing information. - Keep your overview up to date
An inventory that becomes outdated is worthless. Add your new assets immediately and label removed assets as ‘removed’.
Make it a process
Your asset inventory should be dynamic. By this, I mean:
- Establish a procedure for adding or removing assets. This will ensure that the list remains up to date.
- Determine who is responsible for keeping the list current.
- Document changes so that you always know what has changed. This is also a requirement of cybersecurity frameworks.
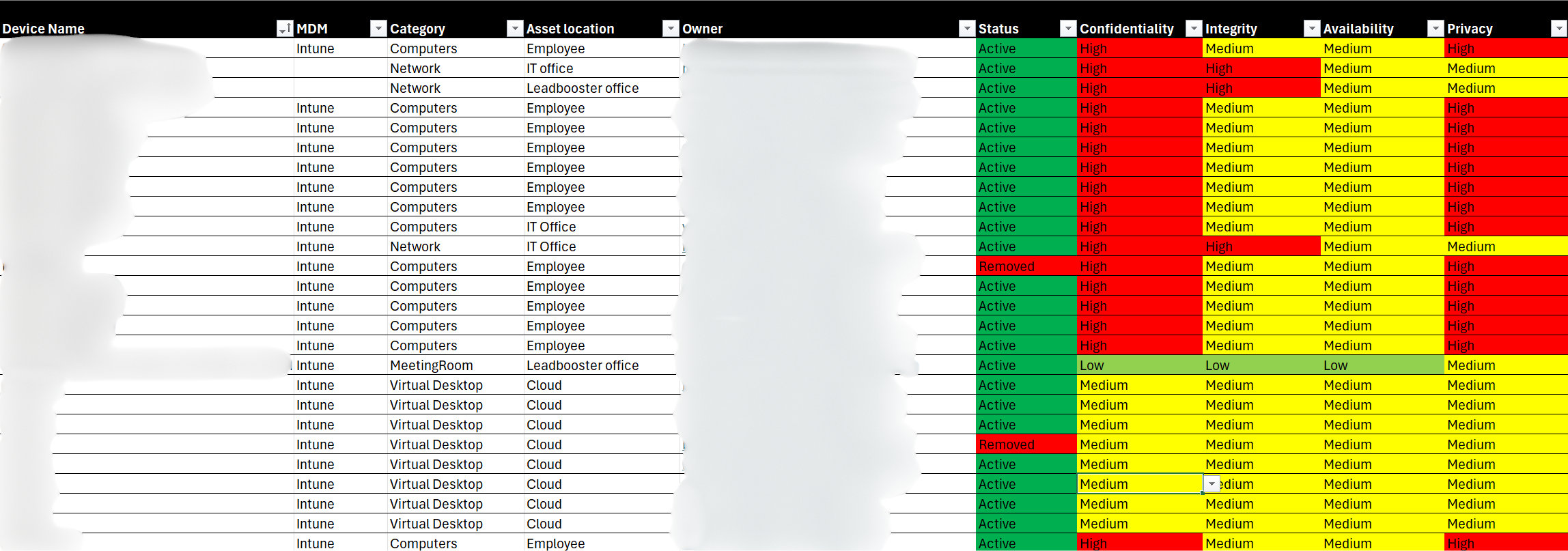
Classify your assets
Not all assets are equally important. That is why it is wise to assess them according to the CIA classification:
- Confidentiality – How sensitive is the data? Who is allowed to see it? Think of customer data or trade secrets.
- Integrity – How important is it that data remains accurate and complete? Think of financial figures or medical records.
- Availability – How critical is it that the asset is always available? Think of a production server or ERP system.
Tip: You can also add Privacy as an additional criterion. This allows you to explicitly take into account how sensitive personal data is and immediately prepare your organization for GDPR legislation.
This is especially important if you process a lot of customer, employee, or patient data.
Why this step is crucial
By scoring your assets on Confidentiality, Integrity, Availability (and possibly Privacy), you will gain:
- A quick overview of which components require maximum protection
- A solid basis for your risk assessment (you base potential risks on your assets)
- Clear priorities before choosing the appropriate security measures
Next time in this series:
In Blog 3 of this series, you will learn how to link your classified assets to threats and vulnerabilities, and how to objectively assess and prioritize risks.